By Chris Saso, CTO & Hallie Barnes, Marketing Manager
Dasher Technologies’ User Technology Forum is an event we put on every year in March to bring together over 350 IT professionals to network the old fashioned way. We provide a forum for our engineering staff to moderate topics that are of interest to our clients. This year we focused on Security and DevOps. The topics resonated with the attendees as demonstrated by the 45% increase in attendees this year!
Miss the event or want to relive it? Watch the highlights here.
Watch the partner and client testimonials here.
Thank you to our sponsors!

Solution Tracks
Value Added Resource Keynote with Chris Saso, Chief Technology Officer
To kick things off, I provided an overview of Dasher and highlighted a theme that is important to us and our clients: Focus on Client Success.  The acronym “VAR” stands for Value Added Reseller, but let’s turn that phrase on its head. At Dasher, it means Value Added Resource. We have the resources that our clients need to assess, design, implement, and optimize solutions to address business challenges. Resellers simply transact business and do not get to know their clients or understand their business challenges. Dasher listens to our clients and provides options and solutions to make our clients successful first and foremost. On the lighter side of this story, Dasher is the patron to our clients. A patron protects and sponsors the client and therefore Dasher views ourselves as the patron for our clients. When you think of Patron, think of Dasher!
The acronym “VAR” stands for Value Added Reseller, but let’s turn that phrase on its head. At Dasher, it means Value Added Resource. We have the resources that our clients need to assess, design, implement, and optimize solutions to address business challenges. Resellers simply transact business and do not get to know their clients or understand their business challenges. Dasher listens to our clients and provides options and solutions to make our clients successful first and foremost. On the lighter side of this story, Dasher is the patron to our clients. A patron protects and sponsors the client and therefore Dasher views ourselves as the patron for our clients. When you think of Patron, think of Dasher!
Solution Track #1 – How to Create a Robust Security Posture
Three of our solution architects, Kellen Christensen, Ashish Shah and Ahmer Bhatty joined two of our account executives, Lucas Melcon and Chris Stewart to talk about security related issues. The focus of the questions steered away from protecting your company perimeter with firewalls and moved towards protecting employees and endpoints using technologies such as Multi-Factor Authentication. The goal of the session was to understand and communicate that it is a journey to make your company secure and so we ended by talking about the “Center for Internet Security – Critical Security Controls” that define a prioritized list of security protocols that a company should follow in order to create a Robust Security Posture.
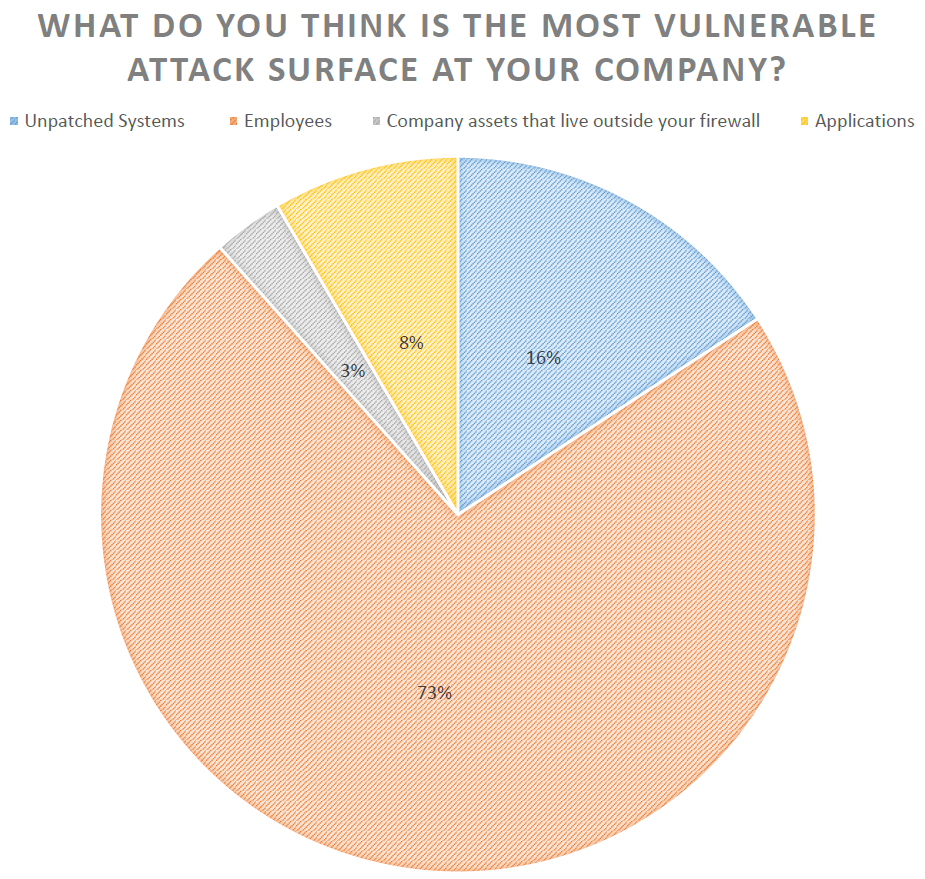
As you see most of our attendees agreed that employee behavior and human actions are the most vulnerable attack surface. So what are companies doing to mitigate this risk? Security training for staff members was a hot topic with opinions on both sides of the argument, whether is effective or not. The general consensus was that the most determined hacker can always find a way into a company given enough time and resources.
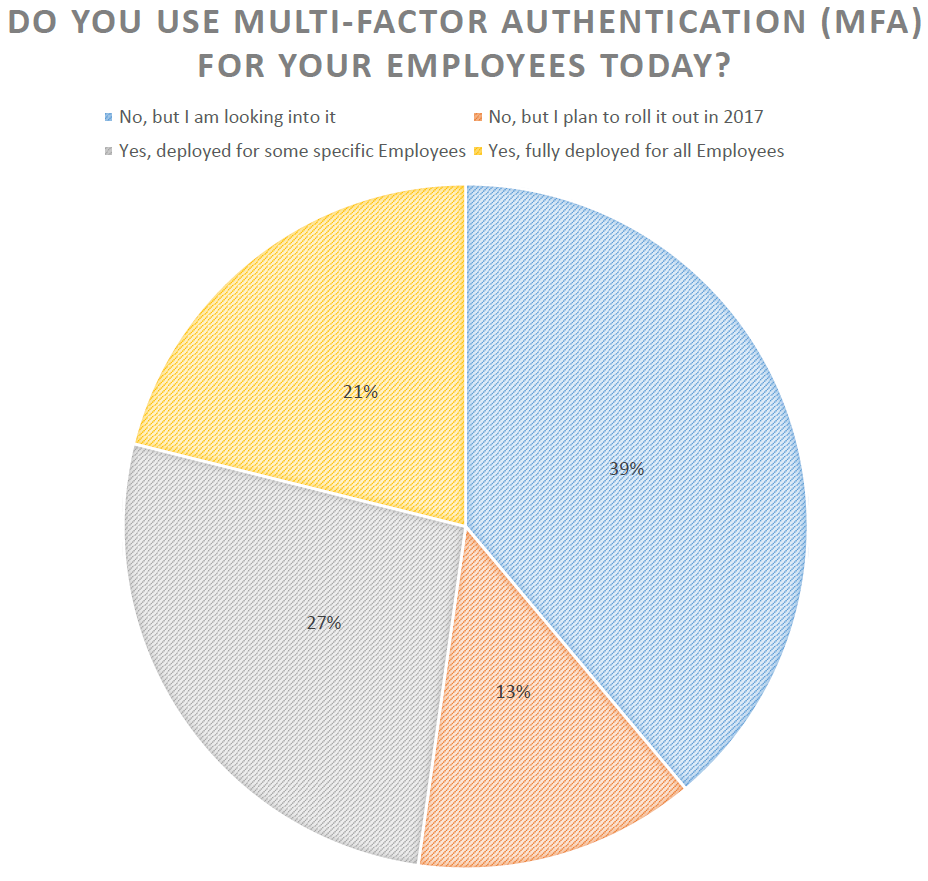
MFA was interesting because there was a fairly even distribution between our attendees on adoption rate, planned rollouts in 2017, with the biggest slice of the pie being folks researching it now.
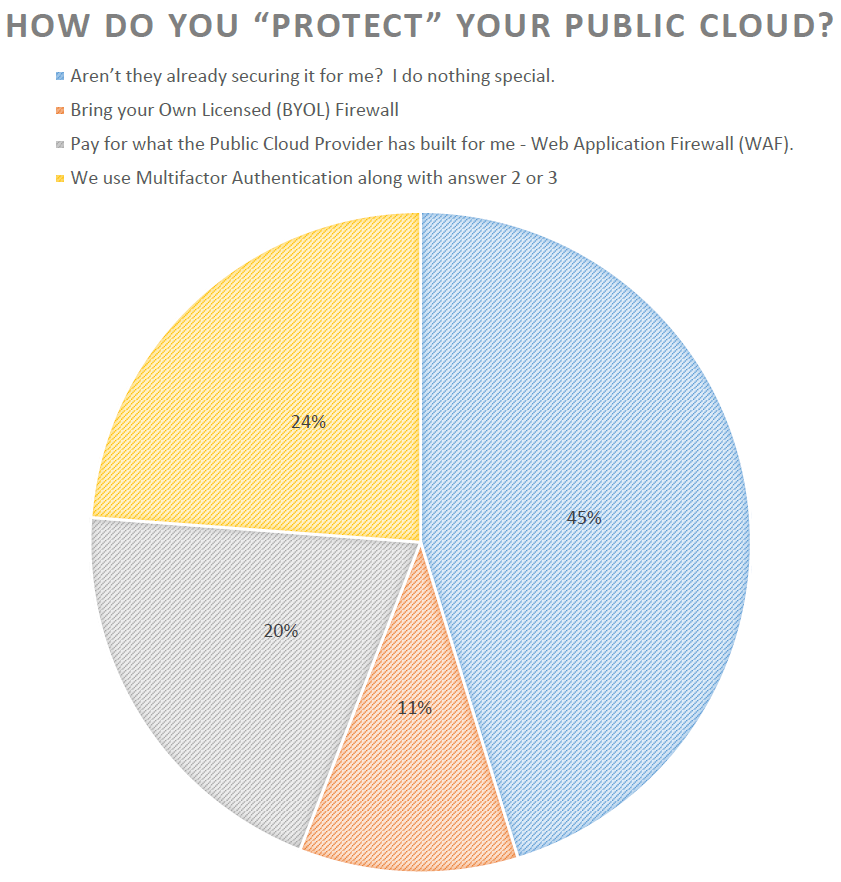
Due to the growing cloud computing trend, we wanted to have one question to gauge the level of effort and attention to securing cloud workloads. This is an area that people may not be paying enough attention to. Just because your workload is in the cloud, does not mean it is secure. Actually, there are many ways to secure your cloud workloads and the audience participated in peer-to-peer discussions. One of our engineers gave an example of an open source database that ships with a standard login/password enabled by default, so that if you don’t proactively go into the settings of the database and “close it down,” anyone with the general credentials could access your database. Not a very secure cloud database. If this was behind your firewall in your own data center this might not be an issue, but if your cloud environment is not adequately secure this could be quite a problem.
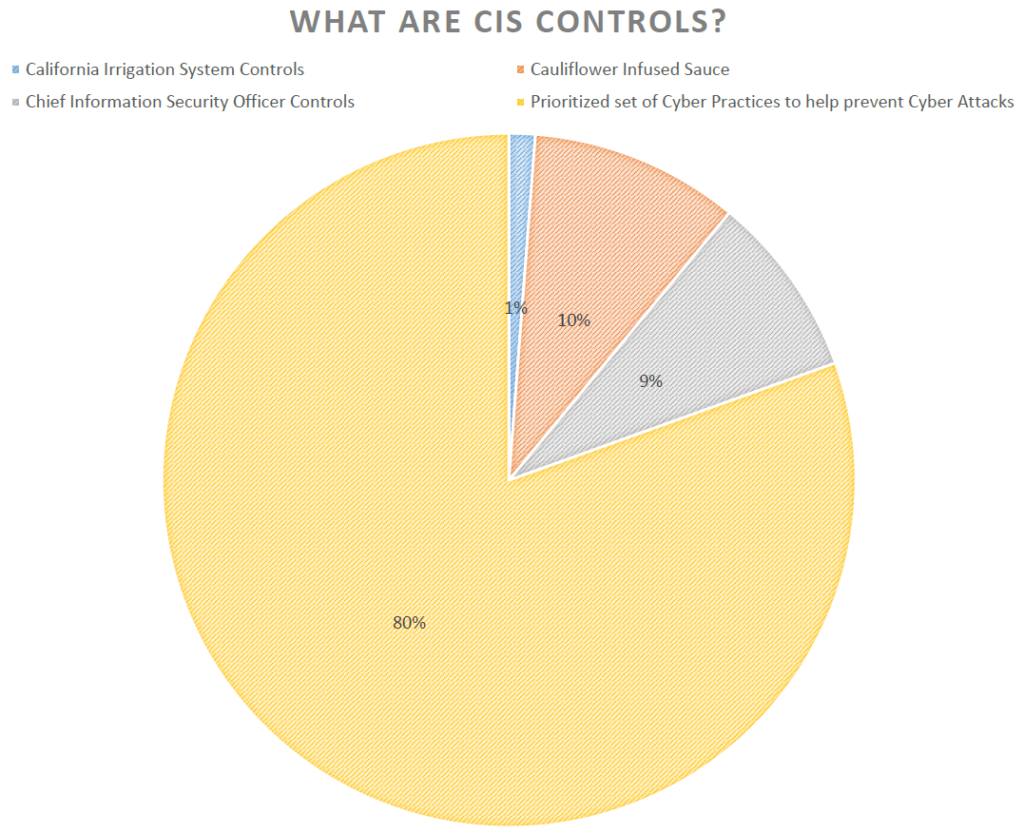
We ended Solution Track #1 by showing the CIS Critical Security Controls . This was the punchline of the session because it showed that there is a plan and a roadmap to security and that it takes many steps to get there. The complete list and a ton of great material can be found at the link above, here are the top 5 things to start with on your journey to a more robust security posture.
- Inventory of Authorized and Unauthorized Devices
- Inventory of Authorized and Unauthorized Software
- Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
- Continuous Vulnerability Assessment and Remediation
- Controlled Use of Administrative Privileges
Solution Track #2 – How to Adopt a DevOps Mindset
In this session, smart guys and veteran solution architects, Isaack Karanja & Bill Jones were joined by pretty guys (account executives) Justin Harrigan and Rob Poole to discuss how companies are developing a DevOps mindset. The hour of this discussion flew by with tons of audience participation covering topics like containers, cloud for automation and orchestration.
We started with a simple question to get the point across that DevOps focuses on collaboration between business units and is a mindset change for companies. Think of it as moving from finger pointing to holding hands!
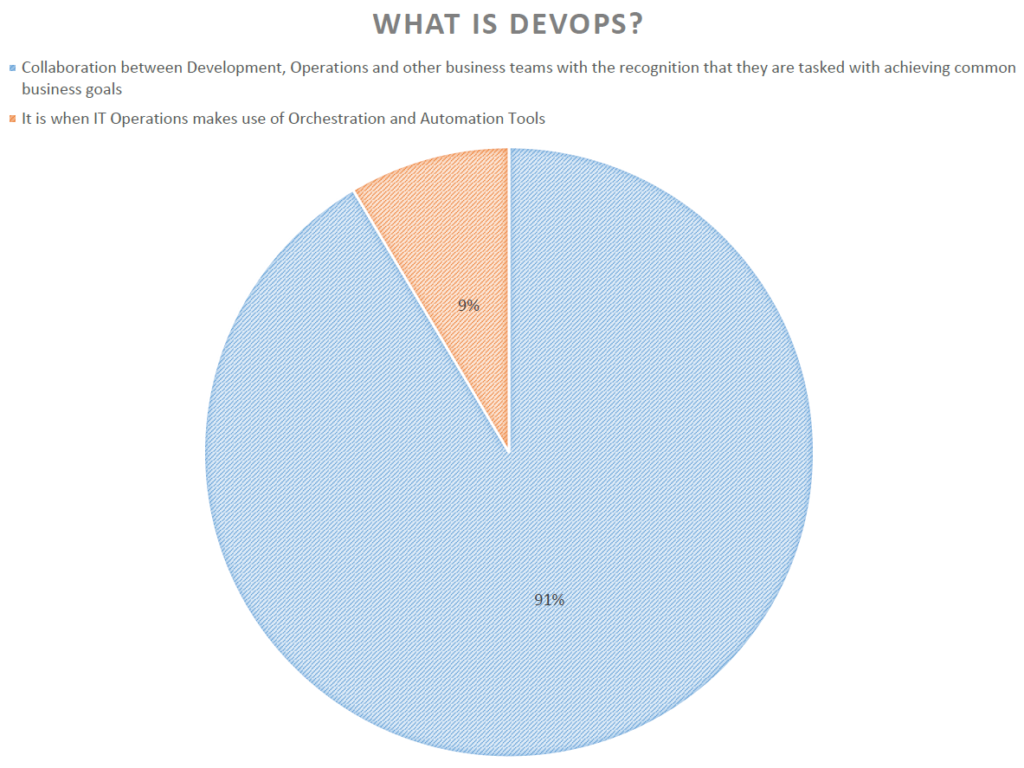
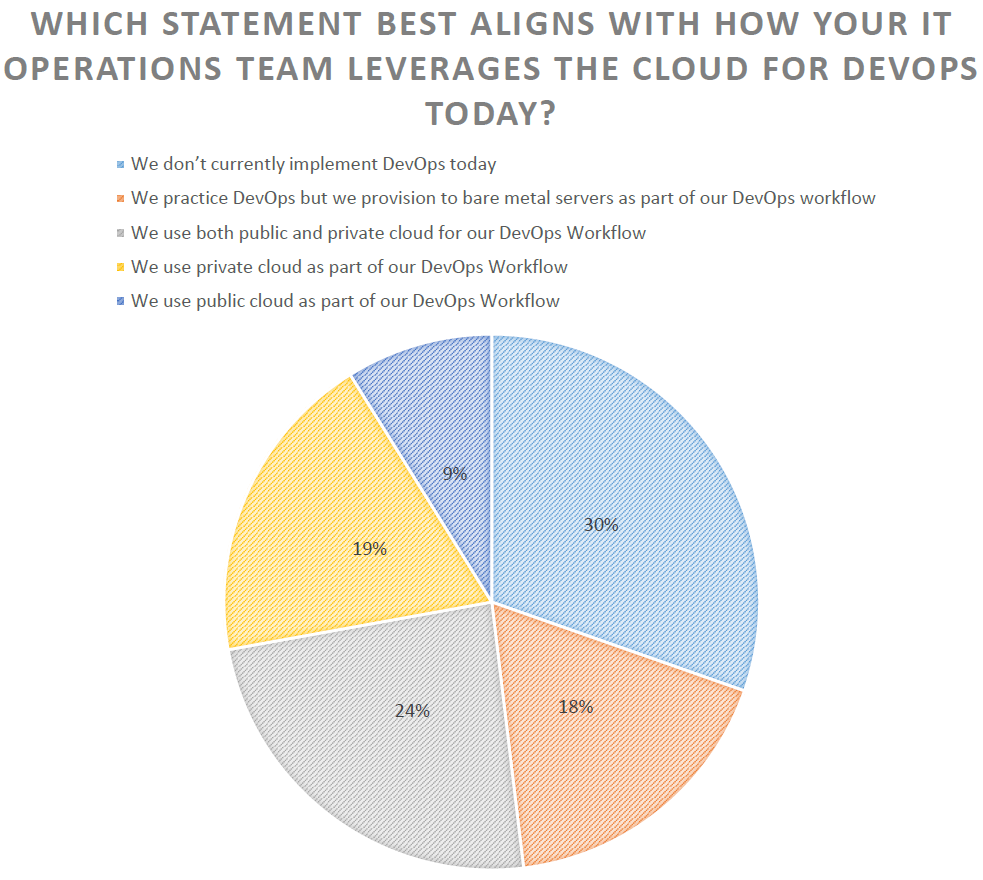
When people say DevOps they probably immediately think of cloud services that can be used to support it. That is very true, but as we can see from this question, DevOps takes a hybrid approach to utilizing technology. The biggest majority of folks that practice DevOps use both public and private resources. Another interesting point is that almost 1/3 of the folks in the room have not yet adopted DevOps at their company. I was impressed that 70% of the folks in the room actually have some DevOps program in place at their companies.
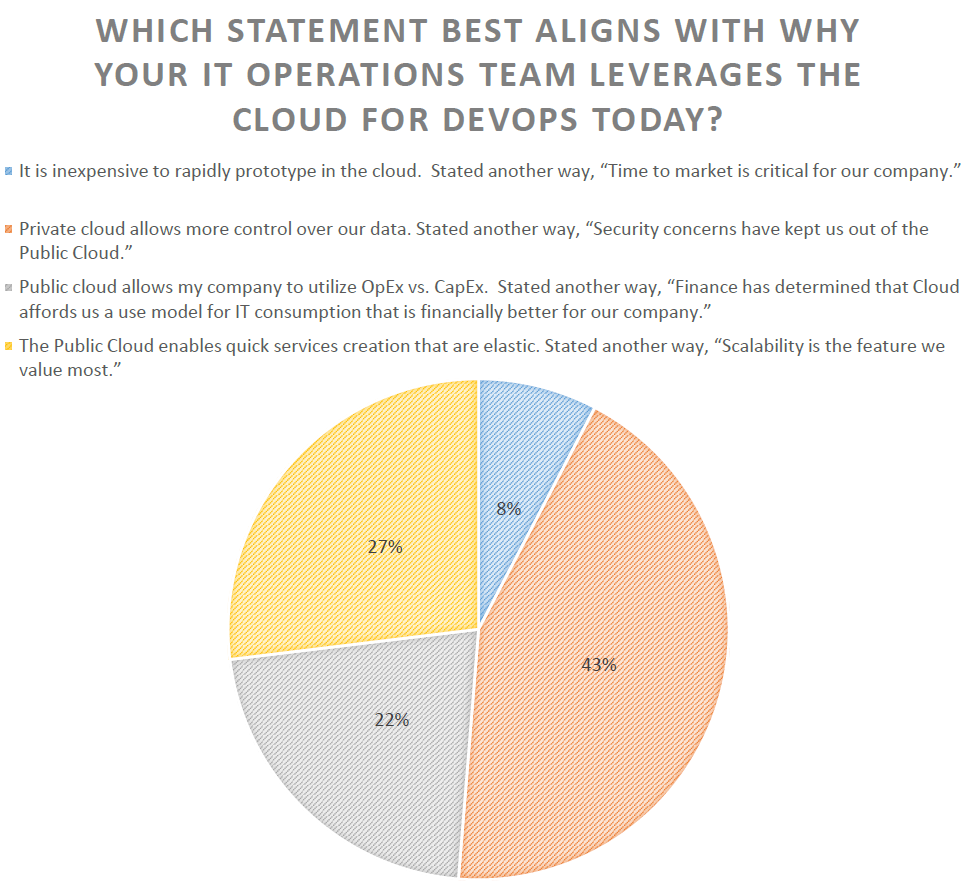
Here is a great look at why IT uses cloud or does not use cloud for DevOps. The majority of the group does not use the cloud for DevOps due to security concerns. This is pretty cool because we had covered this in the morning session. For the folks that do use the cloud it was pretty well split between financial benefits of the pay as you go model and scalability that cloud offers – no surprises there!
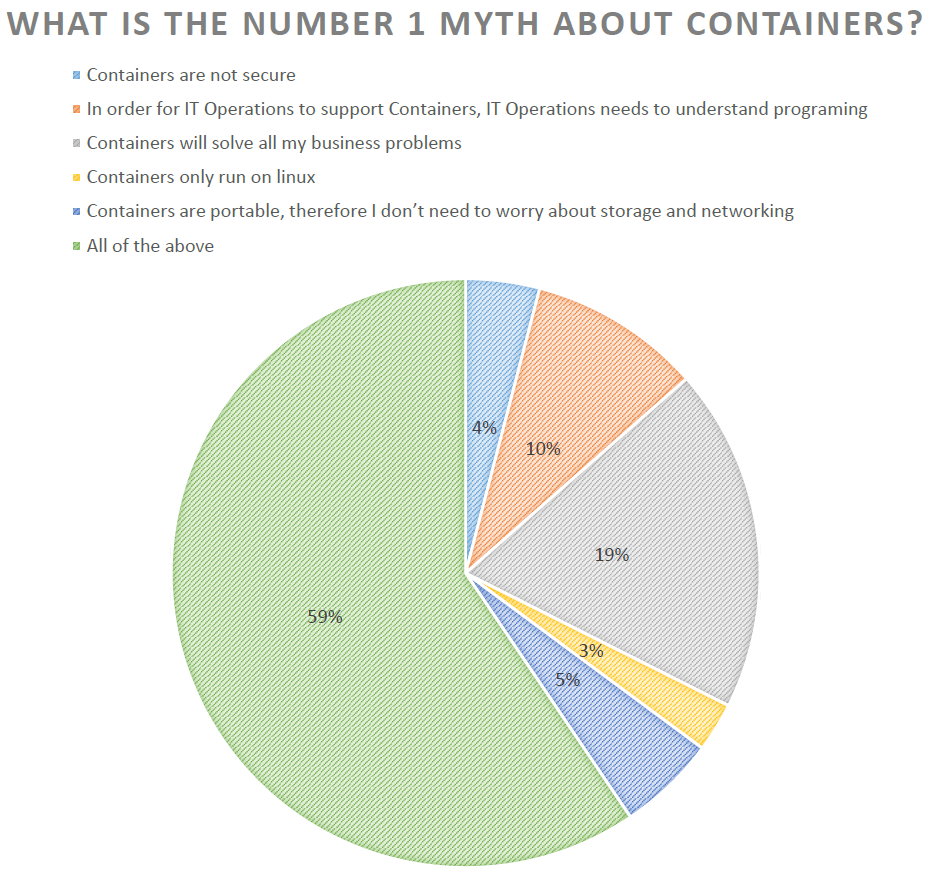
One of the hot topics these days is containers. The next couple questions spurred some discussion about containers and how they are being used. One interesting thing is that over half of the companies don’t use containers at all today. So perhaps there is a lot of buzz and hype, but people are waiting to see the benefits of moving from the current server virtualization strategy to a more application-centric virtualization strategy with containers. Like any new technology, the audience felt containers will be tested in a few areas as the industry determines what the best use cases are for them.
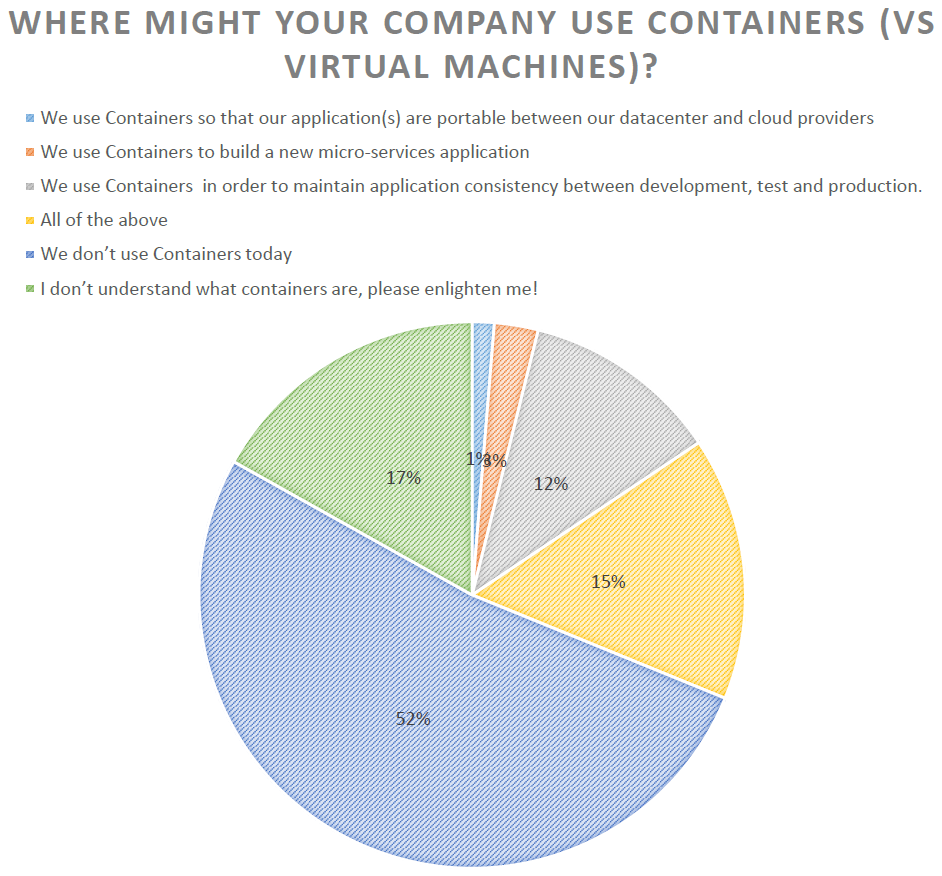
In the end, most people took the attitude that containers are mystical and magical, so let’s see what benefits they will bring and we will jump on when it makes sense for our company.
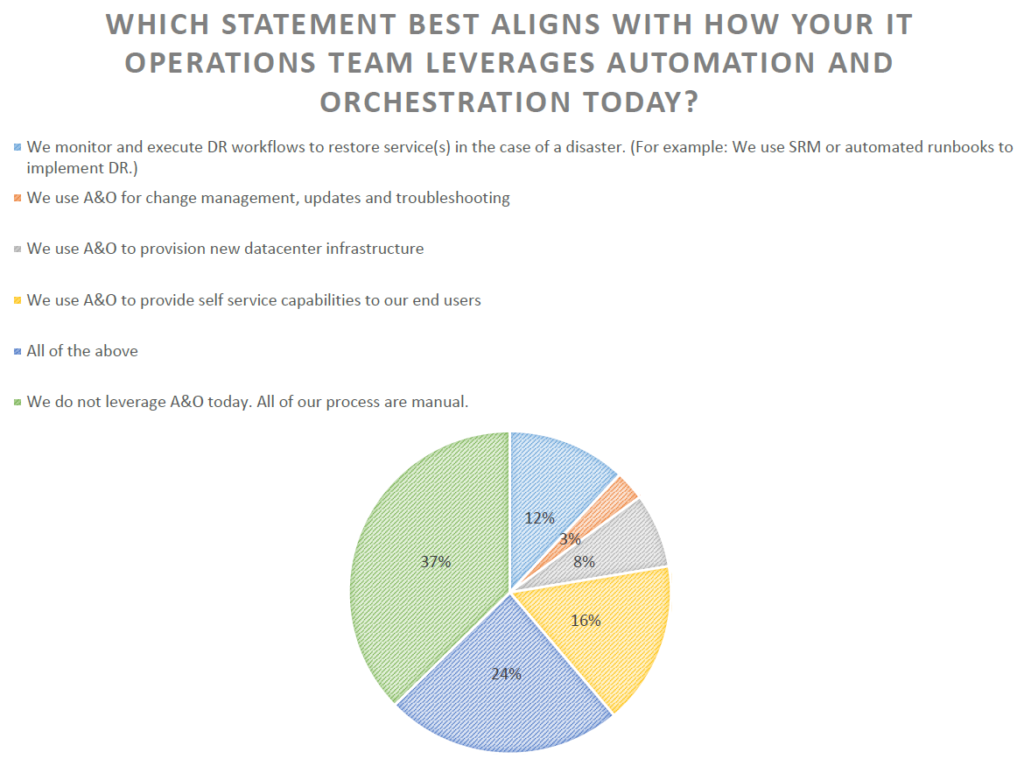
We finished Solution Track #2 by chatting about automation and orchestration. This is truly where IT organizations want to get to; automating redundant and error prone activities to allow IT staff to concentrate on bringing value to the business. Rather than spending time focusing on mundane tasks to provision servers, storage and networking we discussed how orchestration enables IT groups to quickly and efficiently address business challenges and problems.
Sharks vs Capitals Hockey Game
There was a Dasher takeover in the penthouse suites of SAP Center when we gathered to watch the Pacific Conference first place San Jose Sharks beat the Western Conference first place Washington Capitals 4 – 2. We also were witness to the NHL honoring of Joe Thornton for his 1000th career assist that occurred the game prior versus the Winnipeg Jets.
We love our Sharks and the wonderful SAP Center staff. A great time was had by all!
For pictures of this event please find them on our Facebook page.
If you would like to see all the results of our polling or are interested in attending next year, please let us know by filling out this form:

