By: Chris Saso, EVP of Technology & Hallie Barnes, Marketing Coordinator
It is probably no surprise to anyone that one of the fastest growing specializations within Dasher is our security practice. We have hired four additional security focused solution architects over the past 12 months and have expanded our business with existing firewall and next-generation firewall partners like Palo Alto Networks, Check Point, FireEye and Fortinet, while adding new partners such as Sophos to address endpoint security.
Palo Alto Networks was founded by a former Check Point software employee named Nir Zuk. They have been on the scene since 2005 when Nir started to define the next-generation firewall category with a platform approach to security. I appreciate their corporate culture; they are proud of their solutions, but humble about the company and their accomplishments, always keeping the client’s security needs at the forefront of their minds. I just returned from their partner event where I got a nice dose of their culture along with product updates and new product announcements like the PA-7050 high-performance NGFW.
The Palo Alto Networks platform, as shown in the graphic below, consists of their NGFW, their Threat Intelligence Cloud and the Endpoint Protection security products. We expect them to continue to lead and innovate in the area of security solutions that completely address the data center to the endpoint.
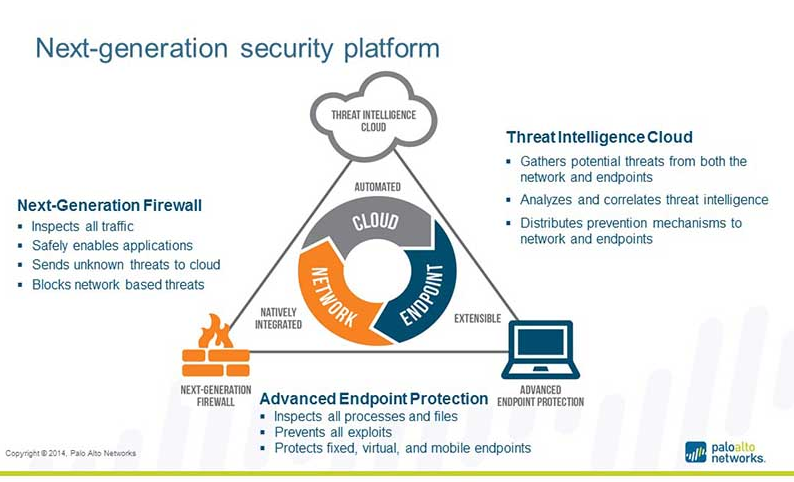
Click on the image for a larger view.
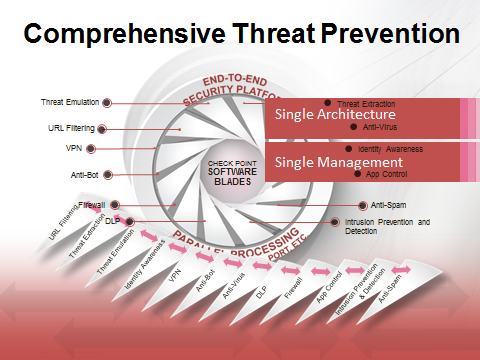
Check Point software, established in 1993 is probably the most established name in security. They invented the idea of a stateful inspection firewall (productized as FireWall-1) and developed one of the world’s first VPN products. Today, Check Point solutions address core data center firewall requirements as well as security in the cloud and at the endpoint. Their unified platform addresses the other major concern of businesses, which is simplified management of IT. If you haven’t given Check Point a look recently you really need to because they have an impressive array of solutions that can address your full set of security requirements.
Click on the image for a larger view.
Fortinet provides network security appliances and security subscription services for carriers, data centers, enterprises and distributed offices. Dasher has deep expertise with their complete FortiGate line of solutions for DCFW (Data Center Firewall), UTM (Unified Threat Management) and NGFW (Next-Generation Firewall). Fortigate has an incredible breadth of solutions and even offers wireless with their recent acquisition of Meru.
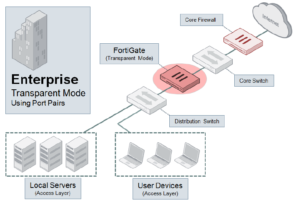
Recently Fortinet rolled out their new Cyber Threat Assessment program, which enables us to perform a threat assessment for our clients utilizing a Fortigate solution setup in transparent mode. We then prepare a report of the activity in their network showing attempts made to breach their network. The summary reports on IPA attacks, Malware and botnet events, and the number of high risk applications detected. The diagram below shows the basic architecture of the PoC.
Click on the image for a larger view.
FireEye’s purpose-built, virtual machine-based security platform continuously protects companies against cyber attacks. As we all know, attackers are changing from individuals to companies that attack corporations for profit. Their messaging is that threats have changed and therefore the products that prevent or detect threats need to change as well.
FireEye provides solutions that respond to 0-day breaches and alert you of their existence. FireEye has a complete incident response team who can be called upon to help people respond when a company determines (or has been told) they have been breached. According to FireEye, the average time an attacker is in your network before they are discovered is 229 days and they are typically discovered by an outside company, not even your own company!
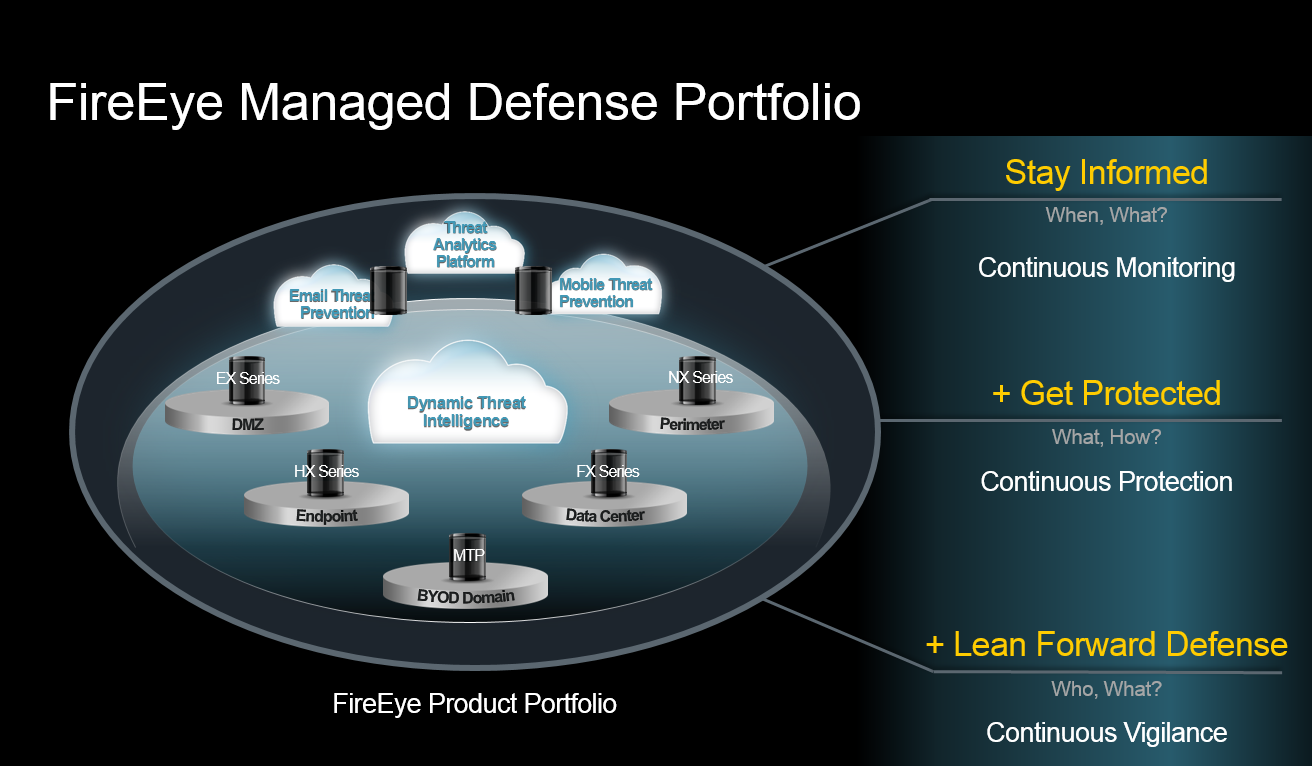
FireEye has created a virtualized environment to incubate threats safely to determine if something will cause damage in your network. They provide products to detect, prevent, analyze and respond to threats. All four pillars are critical in keeping your company safe from security threats. The FireEye Product portfolio is noted below.
Click on the image for a larger view.
Sophos is the biggest security company you might not have heard of, perhaps due to the fact they are based in the United Kingdom. Sophos has an amazing set of tools, but many people are not aware of their breadth of capabilities.They are often pigeon holed into the endpoint protection space, but in fact they are the only vendor that Gartner shows in the leadership quadrant for endpoint, data protection and UTM security solutions. We first became aware of the firm when we began our own research into companies that can offer a complete line of solutions within a unified management framework.
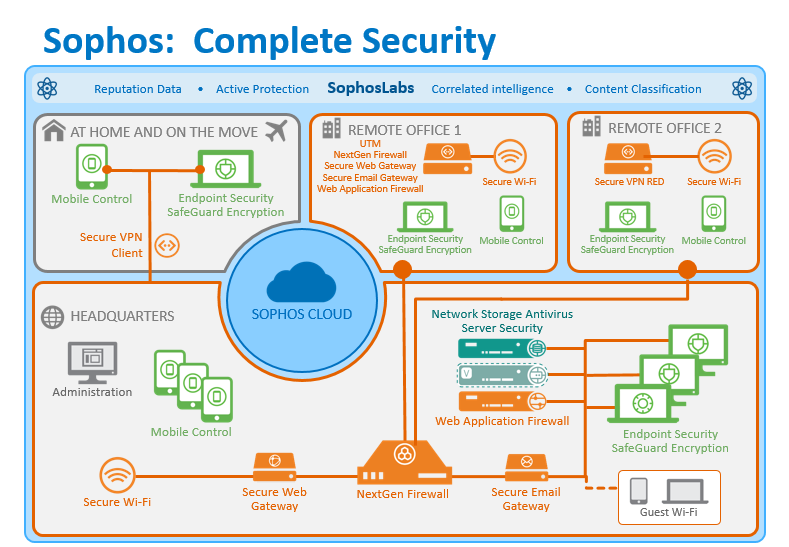
As you can see from looking at the graphic below, Sophos offers Network/UTM, Wireless, Anti-malware, Web, Email and Mobile device security solutions. Similar to other companies discussed on this blog, Sophos also maintains an independent threat research lab to help find and respond quickly to 0-day threats.
Finally, if you want to keep your pulse on the broader security space Sophos has a great blog located here: https://nakedsecurity.sophos.com/
Click on the image for a larger view.