By: Michael Westerfield, Sr. Solution Architect, Dasher Technologies
Container technology is arguably one of the hottest topics in the IT industry today and with its adoption there are a number of details that have to be considered when migrating to a container environment, including security, compute, storage and networking.
vSphere Integrated Containers (VIC) are VMware’s implementation of a containerized environment that tightly ties the containerized environment into the vSphere ecosystem.
This has a number of advantages:
- IT engineer can quickly deploy containers in a familiar VMware environment.
- Allows for the leveraging of the underlying vSphere environment to overcome some of the current shortcomings of containers.
- Currently, containers offer no mechanisms for HA at the container or host level. By utilizing VIC, the hypervisor can provide those services for apps that don’t have HA built in.
- Utilize persistent storage via the same shared storage that is currently being utilized in your vSphere environment.
- Less time spent training staff on managing independent container hosts that can be managed as part of your current vSphere environment with minimal training of your infrastructure team.
- Provides the ability to leverage the core SDDC infrastructure subsystems to support the containerized environment. This integration gives capabilities such as:
- vMotion
- Distributed Resource Scheduling (DRS)
- High-Availability (HA)
- vSAN / iSCSI / NFS shared storage
- Secure isolation, micro segmentation, and RBAC
- SSO via PSC with extension to external identity sources such as Active Directory/LDAP
- Direct deployment to Distributed vSwitch and NSX Logical Switches
- Integration with NSX virtual network infrastructure
- Monitoring and logging visibility via vCenter, vRealize Operations, and VRNI
- Unified, full-stack monitoring and logging visibility
Components
VIC is composed of 4 different parts, all completely Open Source and supported by VMware.
Admiral
This is the container management portal. It provides an interface for DevOps teams to provision and manage containers, and also has the ability to obtain statistics and information about container instances. It provides the ability to combine different containers into an application using either Docker Compose or a proprietary application. It supports containers scaling in and out as well as advanced capabilities, such as approval workflows, which are available when integrated with vRealize Automation.
Harbor
Harbor provides a secure image repository (aka registry) for storing your Docker images. Its purpose is to store and index any images that are used by containers. It extends the Docker distribution open source project by adding functionalities such as security, auditing and identity management.
vSphere Integrated Containers Engine
This is the gateway that allow the VM’s that house your container to be interfaced like a standard Docker container. This engine is Docker remote API-compatible.
PhotonOS
This is a minimal container OS and is used in VIC wherever a Linux guest kernel is required.
While you can download the open source builds of VIC at the VIC Github page (https://vmware.github.io/vic-product/), the official (and supported) builds of vSphere Integrated Containers comes with all vSphere 6.0+ licenses and can be obtained here (http://www.vmware.com/go/download-vic). vSphere 6.5 is recommended for full functionality as the product itself is managed via the 6.5 HTML client and has limited management support on 6.0.
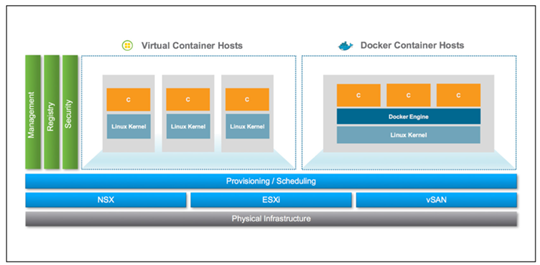
Architecture
In a traditional container environment, containers run as threads within the container host. This has the potential of being a security issue as it opens the possibility of the container accessing the host OS. vSphere Integrated Containers leverage the native constructs of vSphere for provisioning container-based applications into its own container running its own very minimal Linux kernel with just enough code to run a Docker image, thus preventing any issue with containers being accessed from other containers by pushing isolation of the container down to the hypervisor layer that is much better at handling this type of isolation.
This isolation allows IT administrators to deliver a container environment without having to build out a separate, specialized container infrastructure stack. By deploying each container image as a vSphere virtual machine (VM), vSphere Integrated Containers allows these workloads to leverage critical vSphere application availability and performance features such as vSphere HA, vMotion, DRS and more. vSphere Integrated Containers provides these features while still presenting a Docker API to developers of container-based applications.
The VIC engine is the mechanism that provides this Docker API to the container VM’s. It enables the provisioning and management of VMs into vSphere clusters using the Docker binary image format. It enables vSphere admins to pre-allocate certain amounts of compute, networking and storage and provides that to developers as a self-service portal using a familiar Docker-compatible API. It allows developers that already know Docker to develop in containers and deploy them alongside traditional VM-based workloads on vSphere clusters.
VIC is deployed by using a single OVA that then integrates with your vSphere HTML5 client. From the HTML5 client, you can easily deploy your virtual container hosts (although it is called a “host”, which in vSphere we typically think of as a bare metal server, it is actually a VM that acts as an endpoint for your containers) and start provisioning containers.
Conclusion
vSphere Integrated Containers offers a robust solution that enables vSphere shops to quickly get containers up and running in their environment leveraging their current vSphere infrastructure. This environment can be useful for migrating current apps to containers or for in-house development.
For more information go to:

